
Deepfake Detection Project Description
We have presented a deep fake face recognition system using neural network layers and various algorithms in the python programming language.
Since our model is very bulky in size because we are Cloning various GitHub repositories along with the installation of various tarballs. It is advisable to use google Collaboratory for this project.
Overview of deepfake detection code
We are importing the first-order model from GitHub into our notebook.





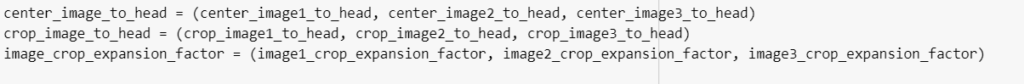
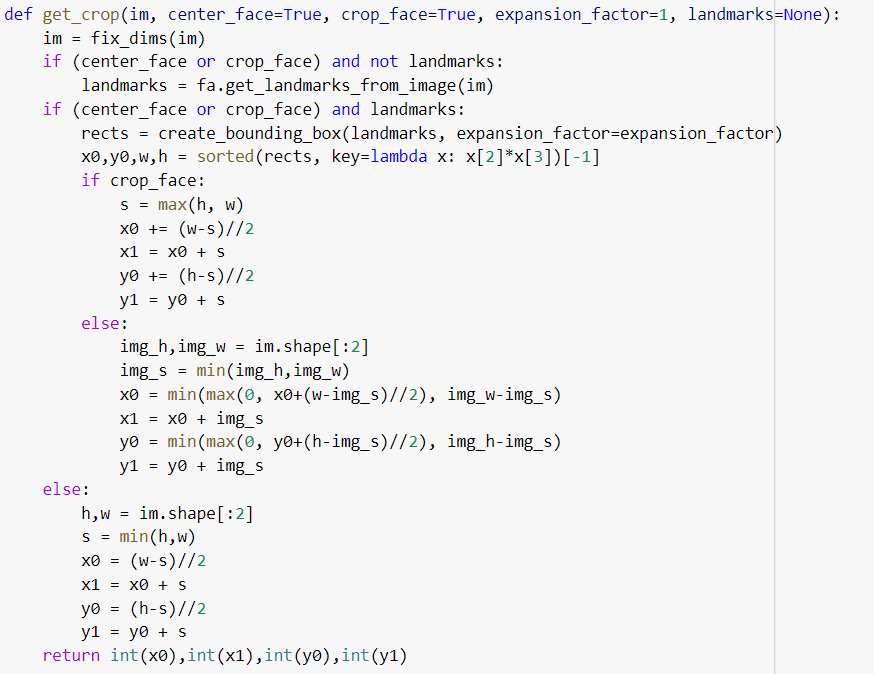
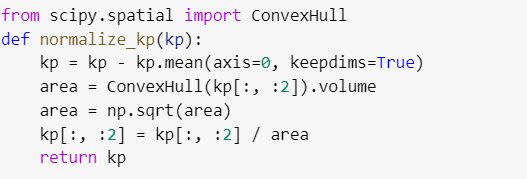
Functions such as create_bounding_box return the stack value that resides in NumPy package. If we talk about functionality, this function mainly deals with the minimum and maximum coordinates of x and y and returns the result.

Let us discuss another function fix_dims( ), which takes an image as the input parameter IT returns the sliced list.
Detect Fake Images Project using Deep learning

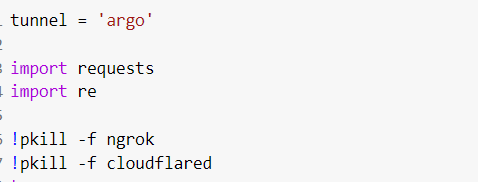
Based on our requirement, we have also imported the request library, regular expression, time, and JSON for our usage. We have used the various functions in which we are accessing the data from localhost based on the value of the tunnel variable that we have initialized as argo in the beginning.
this project is basically is for detecting fake images
Learn Python Today For Free Click Here
Deepfake Deep-learning Project

We have another function full normalise KP that returns the complete normalised value. This function where we have used torch packages.
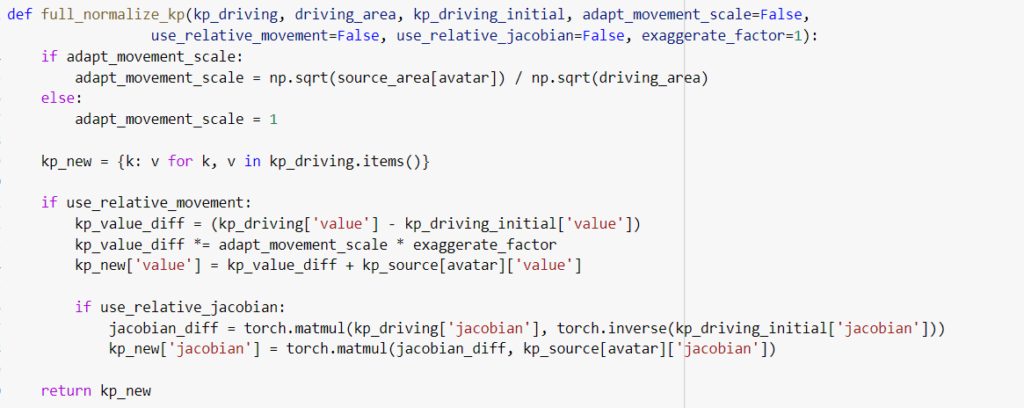
We have also defined a function that generates animation and which returns the transpose of a numpy array where is the result that we receive after the computation of the image parameters.

We have also used a sort of socket programming into our notebook we have used pocket route where we have a private software as a parameter, we are using some of the global variables along with some binary variable in deepfake detection project.

We have used a follow up in which we have used exception handling this basically use exaggeration factor along with other mathematical Parameters.
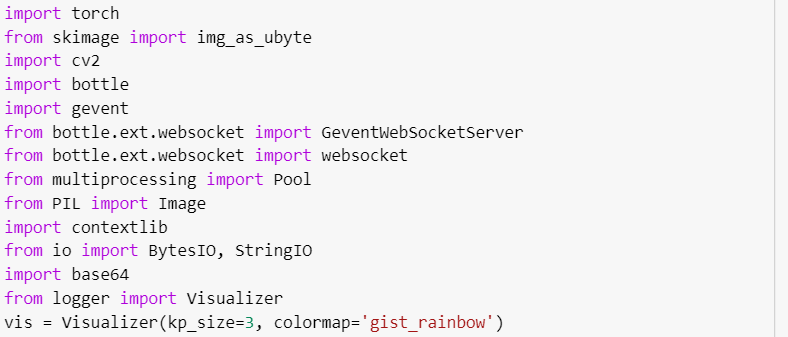
We have imported logging server adaptor from water package by WCF from gevent package websockethandler and create logger from gevent websocket package.
We have created a class G event websocket server in which we are passing server adaptor object. This class consists of two functions run( ) and shutdown( ) handler is a perimeter and we are calling WSGI server function which resides in the event websocket.handler.
Detecting Fake Image using Deepfake Final Year Project

Lastly, I would like to mention that we are using multiprocessing in our project since, this project has a lot of models and github repositories cloned in it. That makes it very difficult for us to process all the thing on single processor. This is the reason we have used to processes in this.

In this way we have created our project.
Also Read:
- Download 1000+ Projects, All B.Tech & Programming Notes, Job, Resume & Interview Guide, and More – Get Your Ultimate Programming Bundle!
- Flower classification using CNN
- Music Recommendation System in Machine Learning
- 100+ Java Projects for Beginners 2023
- Courier Tracking System in HTML CSS and JS
- Test Typing Speed using Python App
- Maximum Subarray Sum: Kadane’s Algorithm
- HackerRank Day 12 Solution in Python: Inheritance
- HackerRank Day 11 Solution in Python: 2D Arrays
- HackerRank Day 10 Solution in Python: Binary Numbers
- Top 15 Machine Learning Projects in Python with source code
- Top 15 Java Projects For Resume
- Top 10 Java Projects with source code
- Best 100+ Python Projects with source code
- Gender Recognition by Voice using Python
- Top 15 Python Libraries For Data Science in 2022
- Top 15 Python Libraries For Machine Learning in 2022
- Drawing Application in Python Tkinter
- Top 10 Final Year Projects for Computer Science Students
- Setup and Run Machine Learning in Visual Studio Code
- Diabetes prediction using Machine Learning
- Library Management System Project in Java
- Bank Management System Project in Java
- CS Class 12th Python Projects
- 15 Deep Learning Projects for Final year
- Machine Learning Scenario-Based Questions
- Customer Behaviour Analysis – Machine Learning and Python
- Maximum Product Subarray in O(N) Time – Leetcode Solution
- NxNxN Matrix in Python 3
- 3 V’s of Big data



